Remote Desktop Protocol, i.e., RDP is a particularly common protocol used to manage the remote windows servers. Administrators often require the guide to check out the user’s activity, such as when the user logged in, authenticated using which IP address, etc. This article will guide you through the step-by-step procedure for tracking and analyzing remote desktop connection logs in the windows server. In short, track & Analyze Remote Desktop Connection Logs in Windows Server
All the logins that occurred on the RDP are logged as events, and each event has an Event ID through which you can determine the actions. RDP connection logs you can view through Event Log Viewer (eventvwr.msc), and understand the reports better, we will split the article into several events and every particular event is assigned with Event ID ,
Network Connection, Authentication, Logon, Session Disconnect/Reconnect, Logoff.
First, login to Windows → Search and Open Event Log Viewer (eventvwr.msc).

Network Connection
Network connection occurred when a particular user tried to establish a network connection to the remote desktop protocol. Event ID for network connection is 1149 when user authentication succeeds. Generally, authentication success is considered a particular user logged correctly in, but in this case the specific user tries to establish a Network Connection.
Network connection logs you can find at: Event Viewer → Applications and Services Logs → Microsoft → Windows → Terminal-Services-RemoteConnectionManager → Operational.
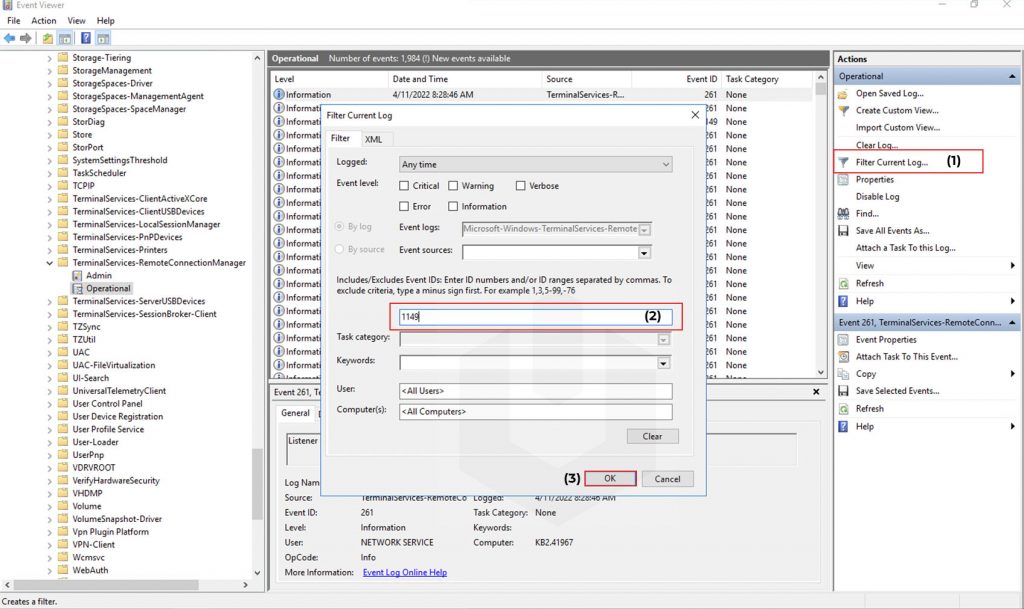
To find the Network Connection Event ID: Click on Filter Current Log → Enter the Event ID 1149 → Click on OK.
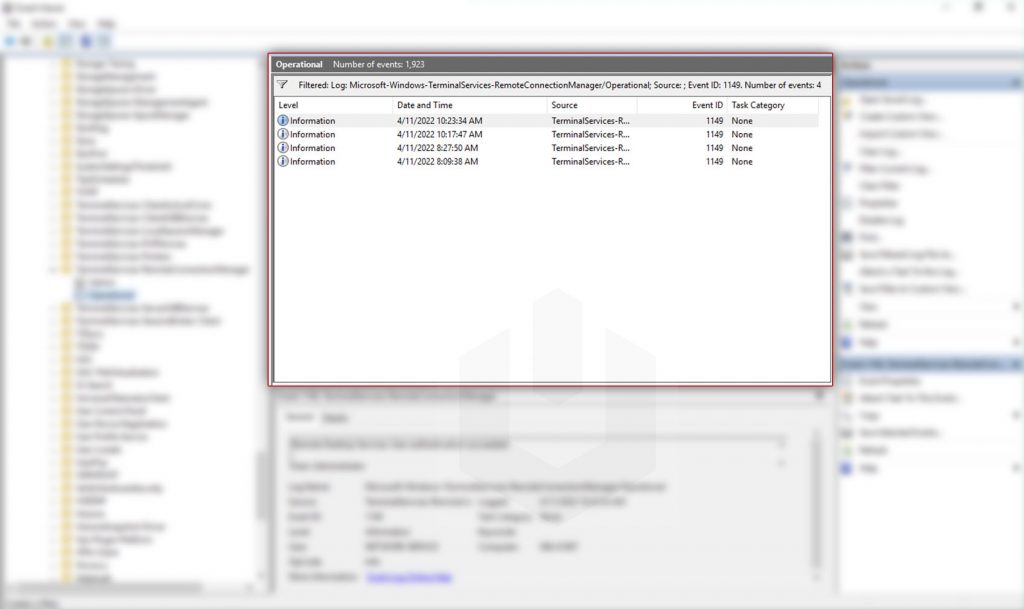
Now, double-click on any of the entry to check the proper details,
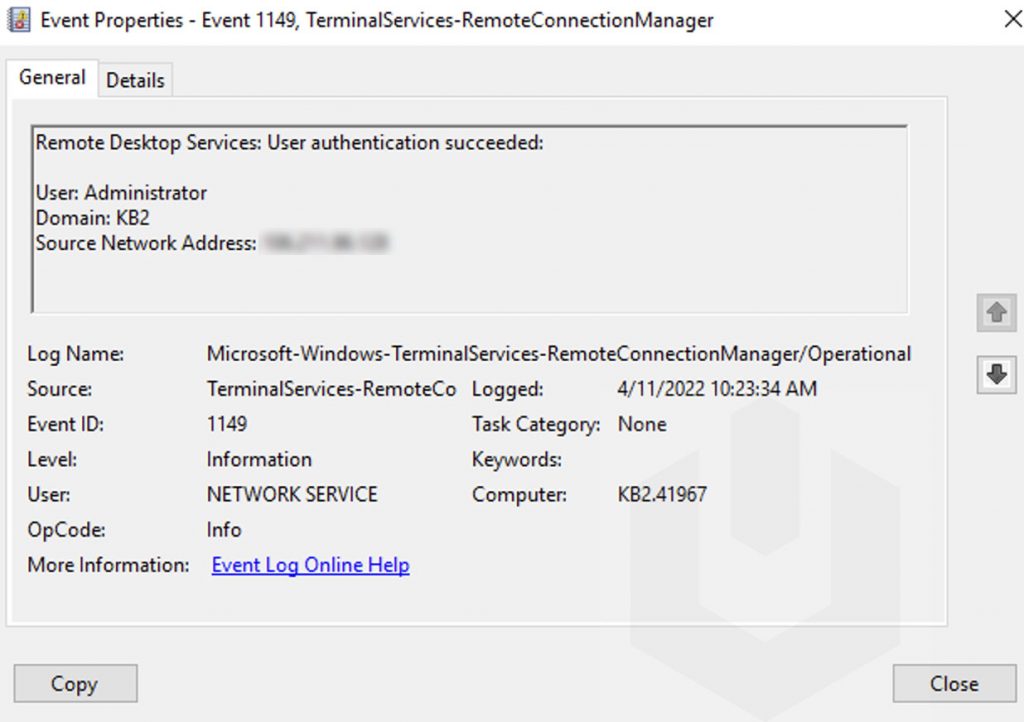
Authentication
Here comes the second part, Authentication. This is the second factor logged in the logs where user authentication is shown with two Event IDs,
- Successful authentication Event ID (where the user logged into the RDP successful): 4624
- Un-successful authentication Event ID (where the user failed to log into the RDP successful): 4625
Furthermore, there are again three Logon types,
- Logon type 5: User authenticated to RDP server console, i.e., mstsc.exe /admin mode.
- Logon type 7: User re-connected to the existing RDP session.
- Logon type 10 or 3: The user tries to create another RDP session while already logged into the RDP.
All the authentication logs you can find at: Event Log Viewer → Windows Logs → Security.
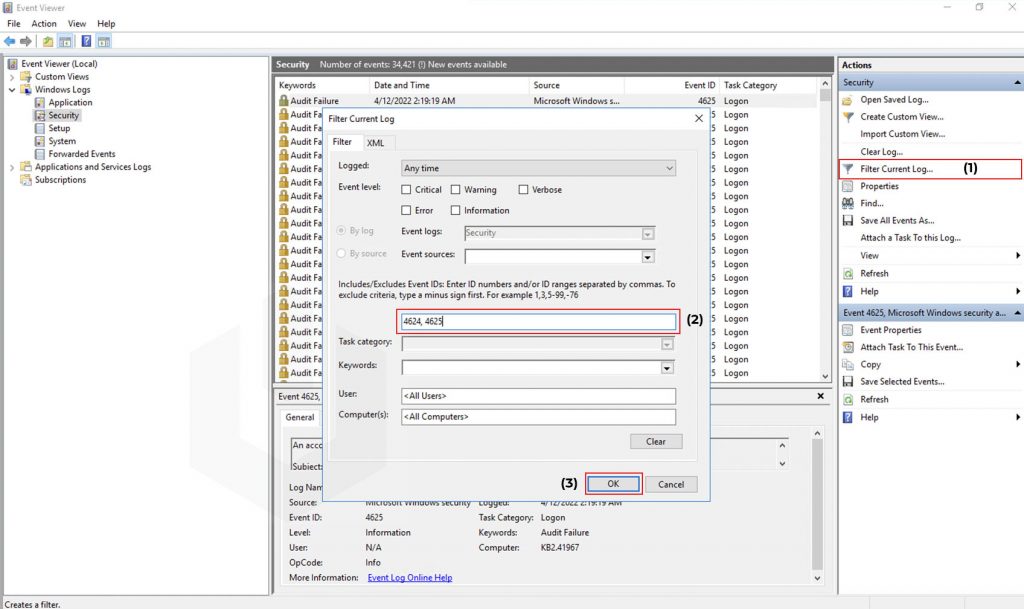
To find the Network Connection Event IDs: Click on Filter Current Log → Enter the Event ID 4624 or 4625 → Click on OK.
Now, double-click on any of the entries to check the proper details,
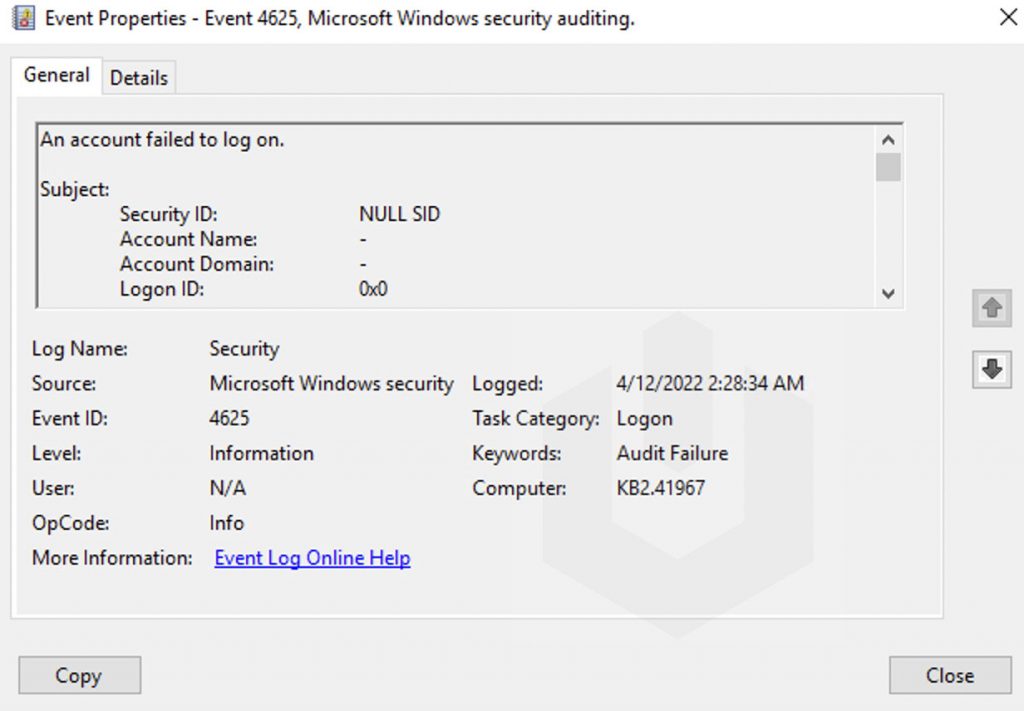
Logon
Logon Event IDs will be logged when a user successfully authenticated in the RDP (Remote Desktop Services: Session logon succeeded). The Event ID for the Logon is 21. You can find the Logon logs at Event Viewer → Applications and Services Logs → Microsoft → Windows → TerminalServices-LocalSessionManager → Operational.
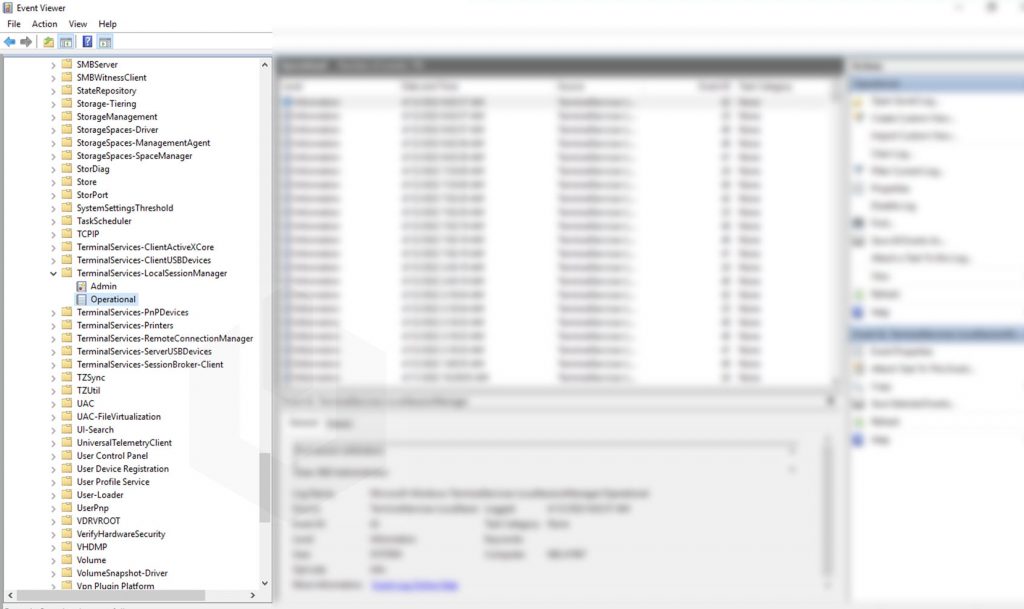
To find the Network Connection Event IDs: Click on Filter Current Log → Enter the Event ID 21 → Click on OK.
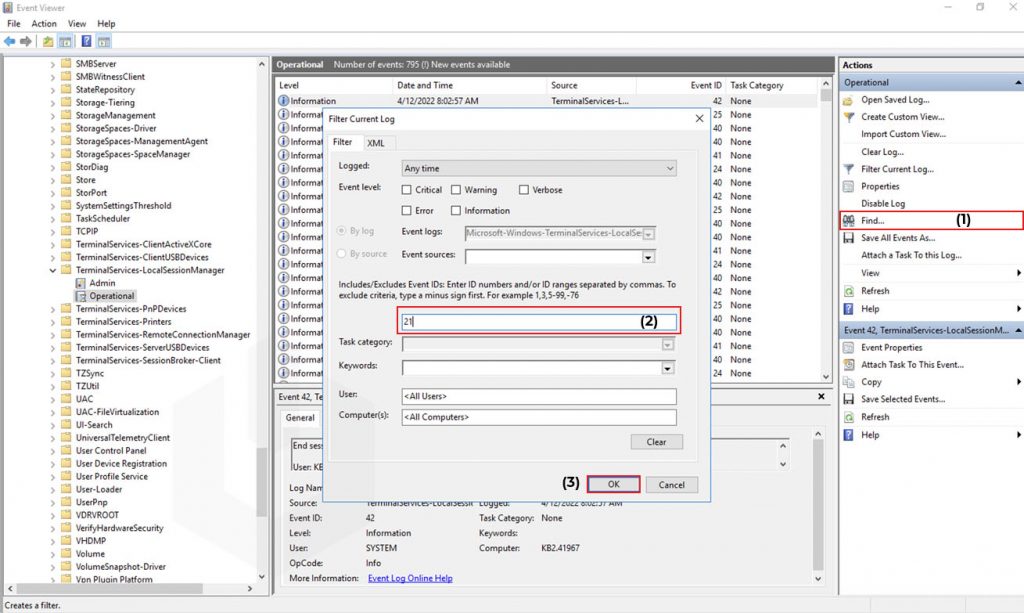
Now, double-click on any of the entries to check the proper details,
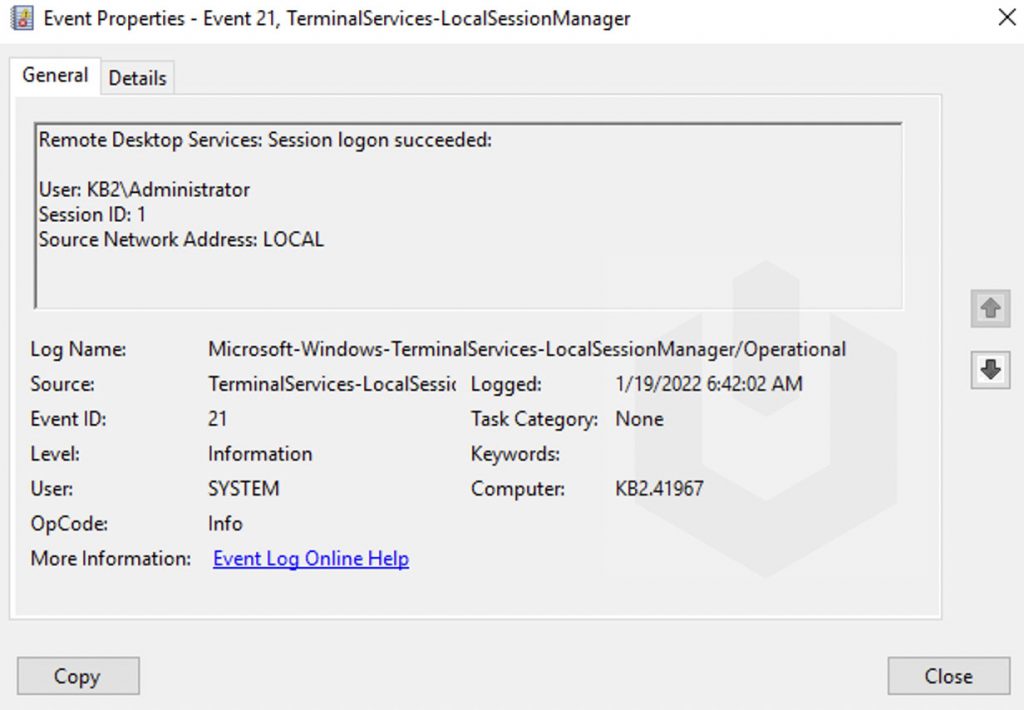
Session Disconnect/Reconnect
Session disconnection and reconnection have various reasons. Every reason for disconnection and reconnection shares different event IDs.
Event ID 24 (Remote Desktop Services: Session has been disconnected): User has disconnected from the RDP session;
Event ID 25 (Remote Desktop Services: Session reconnection succeeded): User has reconnected to the existing RDP session on the server;
Event ID 39 (Session <X> has been disconnected by session <Z>): User has disconnected from the RDP session by selecting the corresponding menu option (instead of just closing the RDP client window). If the session IDs are different, a user has been disconnected by another user (or administrator).
Event ID 40 (Session <A> has been disconnected, reason code <B>). Here you must check the disconnection reason code in the event description. For example:
- Reason code 0 (No additional information is available) User has just closed the RDP client window.
- Reason code 5 (The client’s connection was replaced by another connection) User has reconnected to the previous RDP session.
- Reason code 11 (User activity has initiated the disconnect) User has clicked the Disconnect button in the start menu.
Event ID 4778: User re-connected to RDP session.
Event ID 4779: User disconnected from RDP session.
You can find the Session Disconnect/Reconnect logs at Event Log Viewer → Windows → TerminalServices-LocalSessionManager → Operational.

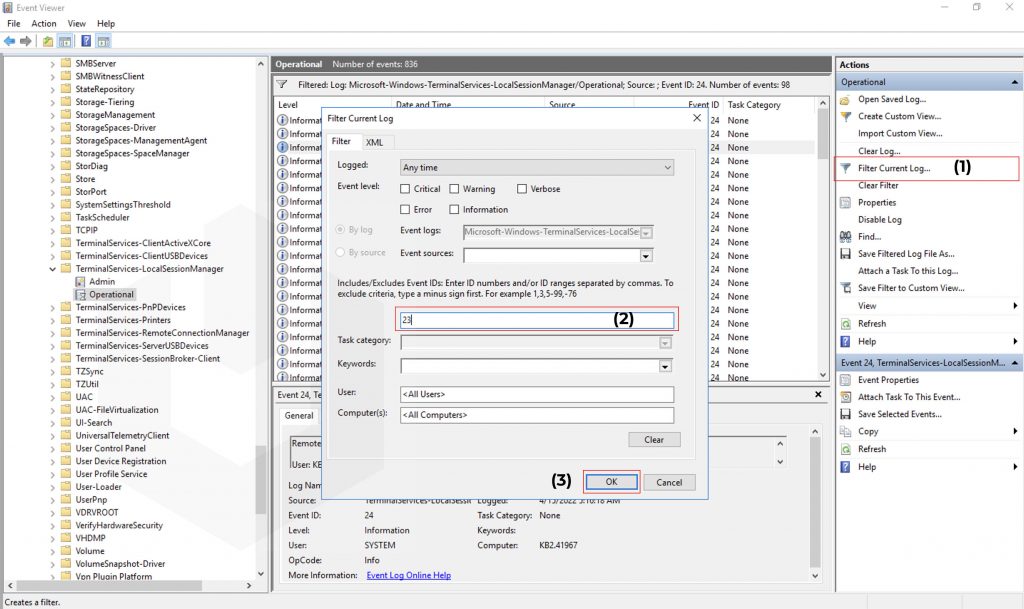
To find the Network Connection Event IDs: Click on Filter Current Log → Enter the Event ID → Click on OK.
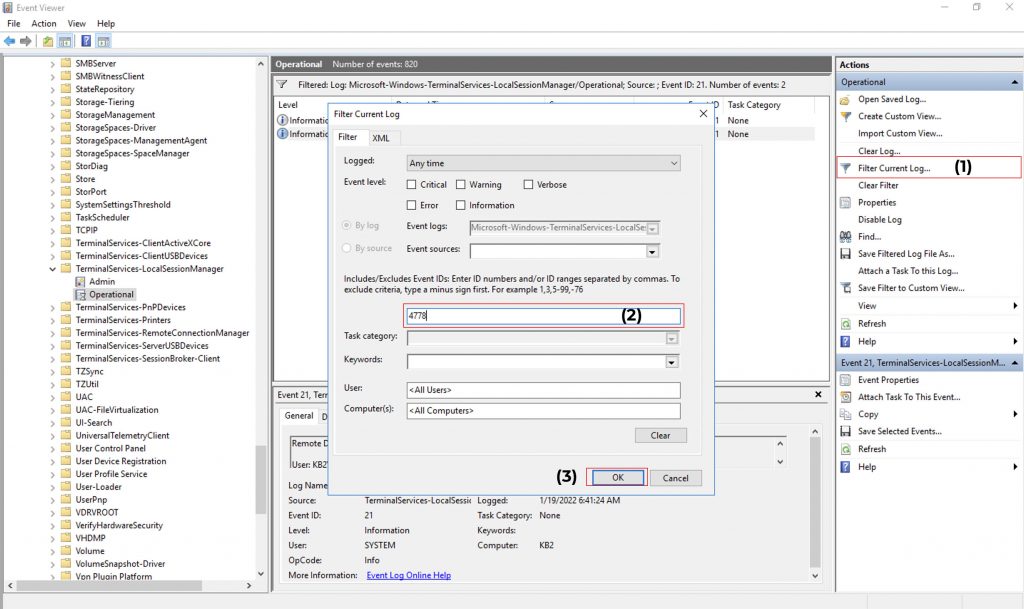
Now, double-click on any of the entries to check the proper details,
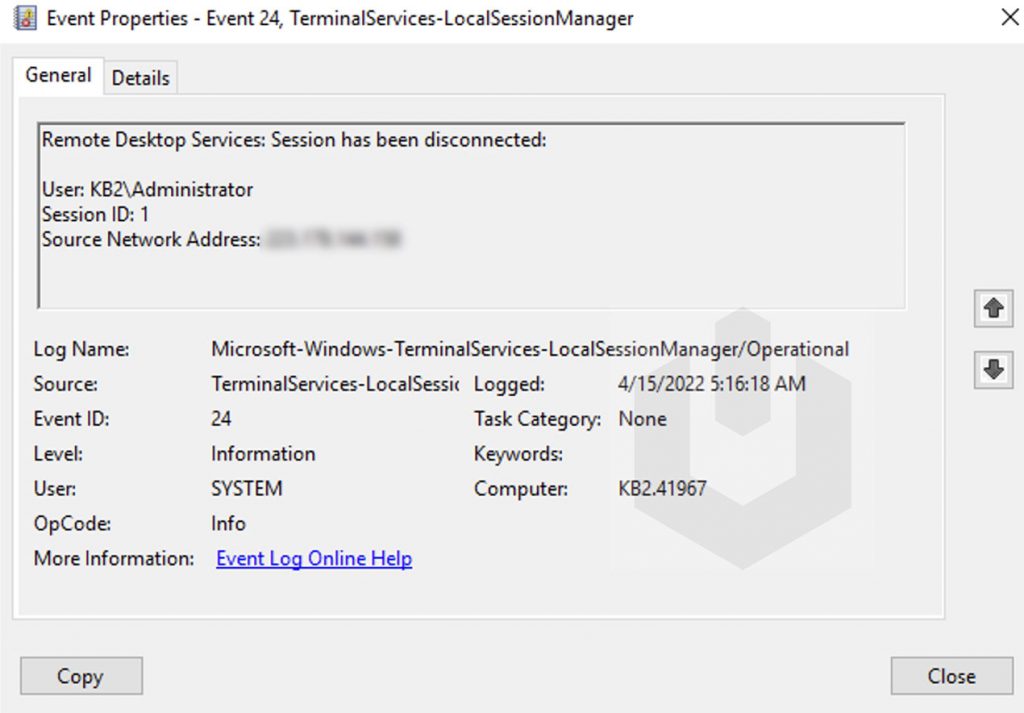
Logoff
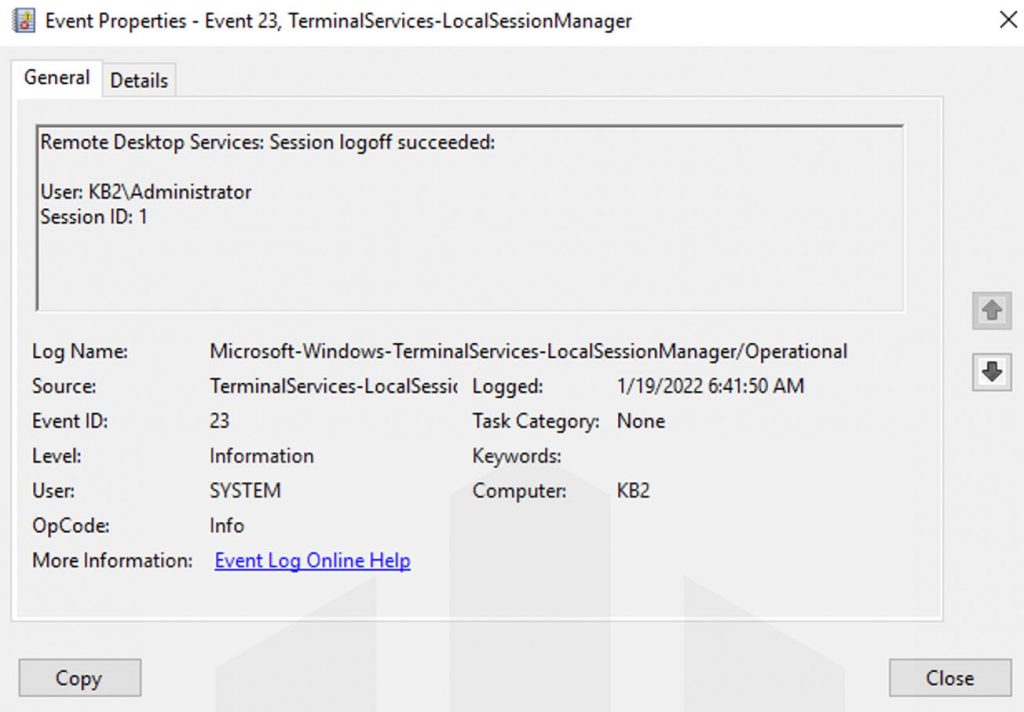
Here comes the last event, which gets logged that helps us when the user ends the session. Logoff shares Event ID 23. Also, you could fine Event ID 4634 (An account was logged off), Event ID 9009 (The Desktop Window Manager has exited with code), Event ID 4647 (User-initiated logoff) and you can find the logs at
Event Log Viewer → Applications and Services Logs → Microsoft → Windows → Terminal-Services-RemoteConnectionManager → Operational.

To find the Network Connection Event IDs: Click on Filter Current Log → Enter the Event ID → Click on OK.
Now, double-click on any of the entries to check the proper details,